上一篇文章我们利用frp技术实现了内网穿透,这篇文章我们来介绍利用openvpn做异地组网。
1、openvpn异地组网
openvpn也是一个client-server技术,需要有客户端和服务端。服务端安装在公司服务器上面,我们可以通过服务端利用路由转发来访问公司局域网任意一台电脑。客户端安装在员工电脑上。
大致架构图如下:
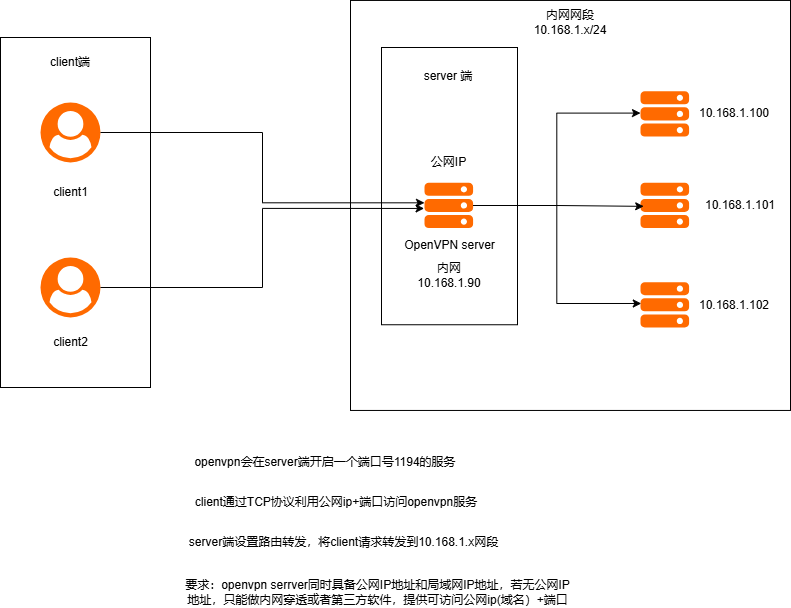
本文以centos7 为例安装部署openvpn
1.1 安装软件
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# yum install -y openvpn easy-rsa
Loaded plugins: fastestmirror
Determining fastest mirrors
base | 3.6 kB 00:00:00
epel | 4.3 kB 00:00:00
extras | 2.9 kB 00:00:00
updates | 2.9 kB 00:00:00
(1/7): base/7/x86_64/group_gz | 153 kB 00:00:00
(2/7): epel/x86_64/updateinfo | 1.0 MB 00:00:00
(3/7): extras/7/x86_64/primary_db | 253 kB 00:00:00
(4/7): epel/x86_64/group | 399 kB 00:00:00
(5/7): epel/x86_64/primary_db | 8.7 MB 00:00:00
(6/7): base/7/x86_64/primary_db | 6.1 MB 00:00:00
(7/7): updates/7/x86_64/primary_db | 27 MB 00:00:00
Resolving Dependencies
--> Running transaction check
---> Package easy-rsa.noarch 0:3.0.8-1.el7 will be installed
---> Package openvpn.x86_64 0:2.4.12-1.el7 will be installed
--> Processing Dependency: libpkcs11-helper.so.1()(64bit) for package: openvpn-2.4.12-1.el7.x86_64
--> Running transaction check
---> Package pkcs11-helper.x86_64 0:1.11-3.el7 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
===============================================================================================================================================================
Package Arch Version Repository Size
===============================================================================================================================================================
Installing:
easy-rsa noarch 3.0.8-1.el7 epel 44 k
openvpn x86_64 2.4.12-1.el7 epel 529 k
Installing for dependencies:
pkcs11-helper x86_64 1.11-3.el7 epel 56 k
Transaction Summary
===============================================================================================================================================================
Install 2 Packages (+1 Dependent package)
Total download size: 628 k
Installed size: 1.5 M
Downloading packages:
(1/3): easy-rsa-3.0.8-1.el7.noarch.rpm | 44 kB 00:00:00
(2/3): openvpn-2.4.12-1.el7.x86_64.rpm | 529 kB 00:00:00
(3/3): pkcs11-helper-1.11-3.el7.x86_64.rpm | 56 kB 00:00:00
---------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 1.4 MB/s | 628 kB 00:00:00
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : pkcs11-helper-1.11-3.el7.x86_64 1/3
Installing : openvpn-2.4.12-1.el7.x86_64 2/3
Installing : easy-rsa-3.0.8-1.el7.noarch 3/3
Verifying : easy-rsa-3.0.8-1.el7.noarch 1/3
Verifying : openvpn-2.4.12-1.el7.x86_64 2/3
Verifying : pkcs11-helper-1.11-3.el7.x86_64 3/3
Installed:
easy-rsa.noarch 0:3.0.8-1.el7 openvpn.x86_64 0:2.4.12-1.el7
Dependency Installed:
pkcs11-helper.x86_64 0:1.11-3.el7
Complete!
1.2创建CA证书
1.2.1 查询 openvpn和easy-rsa的安装路径
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# rpm -ql easy-rsa
/usr/share/doc/easy-rsa-3.0.8
/usr/share/doc/easy-rsa-3.0.8/COPYING.md
/usr/share/doc/easy-rsa-3.0.8/ChangeLog
/usr/share/doc/easy-rsa-3.0.8/README.md
/usr/share/doc/easy-rsa-3.0.8/README.quickstart.md
/usr/share/doc/easy-rsa-3.0.8/vars.example
/usr/share/easy-rsa
/usr/share/easy-rsa/3
/usr/share/easy-rsa/3.0
/usr/share/easy-rsa/3.0.8
/usr/share/easy-rsa/3.0.8/easyrsa
/usr/share/easy-rsa/3.0.8/openssl-easyrsa.cnf
/usr/share/easy-rsa/3.0.8/x509-types
/usr/share/easy-rsa/3.0.8/x509-types/COMMON
/usr/share/easy-rsa/3.0.8/x509-types/ca
/usr/share/easy-rsa/3.0.8/x509-types/client
/usr/share/easy-rsa/3.0.8/x509-types/code-signing
/usr/share/easy-rsa/3.0.8/x509-types/email
/usr/share/easy-rsa/3.0.8/x509-types/kdc
/usr/share/easy-rsa/3.0.8/x509-types/server
/usr/share/easy-rsa/3.0.8/x509-types/serverClient
/usr/share/licenses/easy-rsa-3.0.8
/usr/share/licenses/easy-rsa-3.0.8/gpl-2.0.txt
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# rpm -ql openvpn
/etc/openvpn
/etc/openvpn/client
/etc/openvpn/server
/run/openvpn-client
/run/openvpn-server
/usr/lib/systemd/system/openvpn-client@.service
/usr/lib/systemd/system/openvpn-server@.service
/usr/lib/systemd/system/openvpn@.service
/usr/lib/tmpfiles.d/openvpn.conf
/usr/lib64/openvpn
/usr/lib64/openvpn/plugins
/usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so
/usr/lib64/openvpn/plugins/openvpn-plugin-down-root.so
/usr/sbin/openvpn
/usr/share/doc/openvpn-2.4.12
/usr/share/doc/openvpn-2.4.12/AUTHORS
/usr/share/doc/openvpn-2.4.12/COPYING
/usr/share/doc/openvpn-2.4.12/COPYRIGHT.GPL
/usr/share/doc/openvpn-2.4.12/ChangeLog
/usr/share/doc/openvpn-2.4.12/Changes.rst
/usr/share/doc/openvpn-2.4.12/README
/usr/share/doc/openvpn-2.4.12/README.auth-pam
/usr/share/doc/openvpn-2.4.12/README.down-root
/usr/share/doc/openvpn-2.4.12/README.systemd
/usr/share/doc/openvpn-2.4.12/contrib
/usr/share/doc/openvpn-2.4.12/contrib/OCSP_check
/usr/share/doc/openvpn-2.4.12/contrib/OCSP_check/OCSP_check.sh
/usr/share/doc/openvpn-2.4.12/contrib/README
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/README
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/fwmarkroute.down
/usr/share/doc/openvpn-2.4.12/contrib/openvpn-fwmarkroute-1.00/fwmarkroute.up
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf/client.down
/usr/share/doc/openvpn-2.4.12/contrib/pull-resolv-conf/client.up
/usr/share/doc/openvpn-2.4.12/management-notes.txt
/usr/share/doc/openvpn-2.4.12/sample
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/README
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/client.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/firewall.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/home.up
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/loopback-client
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/loopback-server
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/office.up
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/openvpn-shutdown.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/openvpn-startup.sh
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/roadwarrior-client.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/roadwarrior-server.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/static-home.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/static-office.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/tls-home.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/tls-office.conf
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/xinetd-client-config
/usr/share/doc/openvpn-2.4.12/sample/sample-config-files/xinetd-server-config
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/auth-pam.pl
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/bridge-start
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/bridge-stop
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/ucn.pl
/usr/share/doc/openvpn-2.4.12/sample/sample-scripts/verify-cn
/usr/share/doc/openvpn-2.4.12/sample/sample-windows
/usr/share/doc/openvpn-2.4.12/sample/sample-windows/sample.ovpn
/usr/share/man/man8/openvpn.8.gz
/var/lib/openvpn1.2.2 准备证书环境
#准备证书环境,让证书和 openvpn 配置处于一个目录,方便迁移
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# cp -r /usr/share/easy-rsa/3.0.8/ /etc/openvpn/
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# tree /etc/openvpn/
/etc/openvpn/
├── 3.0.8
│ ├── easyrsa
│ ├── openssl-easyrsa.cnf
│ └── x509-types
│ ├── ca
│ ├── client
│ ├── code-signing
│ ├── COMMON
│ ├── email
│ ├── kdc
│ ├── server
│ └── serverClient
├── client
└── server
4 directories, 10 files
# 将var文件拷贝过去
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# cp /usr/share/doc/easy-rsa-3.0.8/vars.example /etc/openvpn/3.0.8/vars
[root@iZ2ze2ww4eolqqls9pk3q1Z ~]# tree /etc/openvpn/
/etc/openvpn/
├── 3.0.8
│ ├── easyrsa
│ ├── openssl-easyrsa.cnf
│ ├── vars
│ └── x509-types
│ ├── ca
│ ├── client
│ ├── code-signing
│ ├── COMMON
│ ├── email
│ ├── kdc
│ ├── server
│ └── serverClient
├── client
└── server
4 directories, 11 files
初始化证书目录
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa init-pki
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa/pki在当前目录下自动创建了一个pki目录,来存放证书文件
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# tree
.
├── easyrsa
├── openssl-easyrsa.cnf
├── pki
│ ├── openssl-easyrsa.cnf
│ ├── private
│ ├── reqs
│ └── safessl-easyrsa.cnf
├── vars
└── x509-types
├── ca
├── client
├── code-signing
├── COMMON
├── email
├── kdc
├── server
└── serverClient
4 directories, 13 files
自己给自己签发一个证书,使其成为CA机构
使用者发送证书申请文件给CA机构,CA机构签发证书返还给申请者,申请者在自己的服务器上部署证书
生成CA机构证书
生成CA机构证书,我们这里不使用密码
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa build-ca nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating RSA private key, 2048 bit long modulus
....................................+++
.....+++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:
CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/etc/openvpn/easy-rsa/pki/ca.crt #这个文件是新生成的CA自签名证书
查看CA证书
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa show-ca
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Showing details for 'ca'.
This file is stored at:
/etc/openvpn/easy-rsa/pki/ca.crt
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a9:9b:b9:17:9c:8b:28:48
Signature Algorithm: sha256WithRSAEncryption
Issuer:
commonName = Easy-RSA CA
Validity
Not Before: May 15 05:34:28 2025 GMT
Not After : May 13 05:34:28 2035 GMT
Subject:
commonName = Easy-RSA CA
X509v3 extensions:
X509v3 Subject Key Identifier:
59:83:80:2F:D1:42:E7:CA:9F:5C:49:DC:B7:D1:46:80:4E:16:A9:4F
X509v3 Authority Key Identifier:
keyid:59:83:80:2F:D1:42:E7:CA:9F:5C:49:DC:B7:D1:46:80:4E:16:A9:4F
DirName:/CN=Easy-RSA CA
serial:A9:9B:B9:17:9C:8B:28:48
X509v3 Basic Constraints:
CA:TRUE
X509v3 Key Usage:
Certificate Sign, CRL Sign
# 使用openssl 命令查看
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# openssl x509 -in pki/ca.crt -noout -text
1.2.3 配置openVPN服务器证书
生成证书申请文件
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa gen-req server nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
....................+++
...+++
writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-12219.W8pFt1/tmp.TrSrXE'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [server]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/pki/reqs/server.req
# 证书申请文件
key: /etc/openvpn/easy-rsa/pki/private/server.key
# 私钥审核申请文件,颁发机构证书
颁发机构证书,第一个 server 指证书类型,第二个server 指申请文件
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa sign-req server server
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a server certificate for 825 days:
subject=
commonName = server
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-12279.HW1qWw/tmp.7JNUtm
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'server'
Certificate is to be certified until Aug 18 05:50:40 2027 GMT (825 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa/pki/issued/server.crt
# CA机构根据申请文件签发的证书创建Dh密钥
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa gen-dh1.2.4 配置openvpn客户端证书
客户端证书交由具体使用者作为登录 VPN 服务器的凭证,有效期不能太长
可以通过修改vars文件中的set_var EASYRSA_CERT_EXPIRE 参数
生成客户证书申请文件
为用户tom申请文件
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa gen-req tom nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
....................+++
...+++
writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-12385.6aWCog/tmp.Yj1G5e'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [tom]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/pki/reqs/tom.req
key: /etc/openvpn/easy-rsa/pki/private/tom.key签发客户端证书
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa sign-req client tom
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a client certificate for 825 days:
subject=
commonName = tom
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-12413.JJ7qwH/tmp.ssJuZ1
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'tom'
Certificate is to be certified until Aug 18 06:04:14 2027 GMT (825 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa/pki/issued/tom.crt
# 查看证书命令
./easyrsa show-cert tom1.2.5 总结
通过vars文件,创建ca证书
build-ca nopass
创建server证书和私钥
gen-rep server nopass
sign-rep server server
创建dh.pem文件
gen-dh
创建client 证书和私钥
gen-rep client nopass
sign-rep client tom1.2.6 整理文件
将服务端相关证书文件复制到server目录下
cp /etc/openvpn/easy-rsa/pki/ca.crt /etc/openvpn/server/
cp /etc/openvpn/easy-rsa/pki/issued/server.crt /etc/openvpn/server/
cp /etc/openvpn/easy-rsa/pki/private/server.key /etc/openvpn/server/
cp /etc/openvpn/easy-rsa/pki/dh.pem /etc/openvpn/server/
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ls -lh /etc/openvpn/server/
total 20K
-rw------- 1 root root 1.2K May 15 14:20 ca.crt
-rw------- 1 root root 424 May 15 14:22 dh.pem
-rw------- 1 root root 4.5K May 15 14:21 server.crt
-rw------- 1 root root 1.7K May 15 14:21 server.key
将客户端相关证书文件复制到client目录下
cp /etc/openvpn/easy-rsa/pki/ca.crt /etc/openvpn/client/tom/
cp /etc/openvpn/easy-rsa/pki/private/tom.key /etc/openvpn/client/tom/
cp /etc/openvpn/easy-rsa/pki/issued/tom.crt /etc/openvpn/client/tom/
ls -lh /etc/openvpn/client/tom
2.1 openvpn配置
2.1.1 服务端配置文件说明
配置文件默认不存在,需要手动创建
cp /usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf /etc/openvpn/
vim server.conf
port 1194
proto tcp
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key
dh /etc/openvpn/server/dh.pem
server 10.8.0.0 255.255.255.0
push "route 10.168.1.0 255.255.255.0"
keepalive 10 120
cipher AES-256-CBC
compress lz4-v2
push "compress lz4-v2"
max-clients 2048
user root
group root
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 3
mute 20
# 创建文件日志目录
mkdir /var/log/openvpn/
# 创建自启动
systemctl enble --now openvpn@server.service2.1.2 客户端配置
vim client/tom/client.ovpn
client
dev tun
proto tcp
remote x.x.x.x 1194 #生产中为OpenVPN服务器的FQDN或者公网IP
resolv-retry infinite
nobind
ca ca.crt
cert tom.crt
key tom.key
remote-cert-tls server
cipher AES-256-CBC
verb 3 #此值不能随意指定,否则无法通信
compress lz4-v2 2.2 服务端配置路由转发以访问内网网段
echo net.ipv4.ip_forward = 1 >> /etc/sysctl.conf
sysctl -p
sysctl -p | grep ip_forward在OpenVPN server 主机上设置 SNAT 转发,将从 10.8.0.0/24 网段主机请求的源IP转换成本机 IP(伪装)
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j MASQUERADE
# 查看postrouting链
iptables -t nat -vnL POSTROUTING
Chain POSTROUTING (policy ACCEPT 6132 packets, 406K bytes)
pkts bytes target prot opt in out source destination
3 180 MASQUERADE 0 -- * * 10.8.0.0/24 !10.8.0.0/24
# 查看forword链
iptables -vnL FORWARD
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
# 注意如果forword链的policy是DROP,需要同意转发
iptables -A FORWARD -i tun0 -o ens192 -j ACCEPT # 允许 VPN 客户端访问本地网络
iptables -A FORWARD -i ens192 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT #允许回包将 OpenVPN server 主机的 iptables 规则设置为开机加载,保证重启后有效
echo 'iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j MASQUERADE' >> /etc/rc.d/rc.local
# 如果forword 为 ACCEPT 则无需设置下面两行
echo 'iptables -A FORWARD -i tun0 -o ens192 -j ACCEPT' >> /etc/rc.d/rc.local
echo 'iptables -A FORWARD -i ens192 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT' >> /etc/rc.d/rc.local
chmod a+x /etc/rc.d/rc.local截止到上面我们已经实现了异地组网的需求,某些用户可能还会对安全性方面存在担忧,下面我们介绍一下openvpn的安全管理功能。
3.1 openvpn安全管理
3.1.1 启动安全增强功能
服务端配置
openvpn --genkey --secret /etc/openvpn/server/ta.key
ll /etc/openvpn/server/ta.key
# 修改服务端配置文件
vim /etc/openvpn/server.conf
tls-auth /etc/openvpn/server/ta.key 0 #增加此行,服务端后面要跟数字0,客户端后面数字是1
#重启服务端,客户端会断开连接,小图标会变成黄色
systemctl restart openvpn@server客户端配置
# 将ta.key 放置到客户端的config文件夹下
# 修改客户端配置文件,加上下面一行
tls-auth ta.key 1
# 重连客户端3.1.2 设置客户端私钥密码
# 在申请客户端证书时输入密码
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa gen-req tom # 注意此处没有nopass
[root@iZ2ze2ww4eolqqls9pk3q1Z easy-rsa]# ./easyrsa sign-req client tom
3.1.3 客户端登陆用户名和密码
在证书的基础上可以再新增用户名密码校验,以提高安全性
服务端配置
# 添加三行
vim /etc/openvpn/server.conf
script-security 3 #允许使用自定义脚本
auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env #指定自定义脚本路径
username-as-common-name #开启用户密码验证准备脚本
脚本下载地址:
https://github.com/imldy/openvpn-checkpsw/blob/main/checkpsw.sh
http://www.openvpn.se/files/other/checkpsw.sh #官方下载地址,己打不开
vim checkpsw.sh
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman <mathias@openvpn.se>
#
# This script will authenticate OpenVPN users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
PASSFILE="/etc/openvpn/psw-file"
# LOG_FILE="/var/log/openvpn-password.log" 修改文件路径
LOG_FILE="/var/log/openvpn/openvpn-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
# 添加可执行权限
chmod a+x checkpsw.sh
# 重启服务
systemctl restart openvpn@server客户端配置
#在client.ovpn 中加上如下行
auth-user-pass


